The original Japanese version is available here.
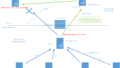
Last time, we accomplished adding the signature using DKIM. In this experiment, we plan to have the risky Windows PC as the client at the end, so Virus Check is mandatory. This time, we plan to use ClamAV, a well-known antivirus in Linux environment, with MILTER to perform Virus Check. There are many Virus Checkers for Windows in the world, but the number of options decreases dramatically when it comes to Linux. And when it comes to FreeBSD, the options become even more limited when it comes to free use. Although it may not seem the latest, I found a comparison table and would like to share it as a reference. In /usr/ports/security, there are two types of ClamAV: ClamAV and ClamAV-LTS. Which one is better depends on the person, but I, who likes new things, would like to try using the newer ClamAV with a higher engine version.
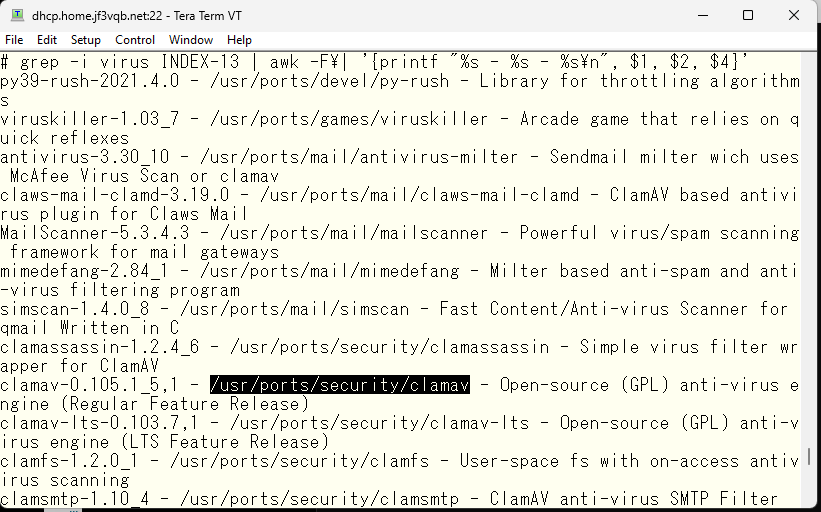
Perform make install clean in the /usr/ports/security/clamav directory.
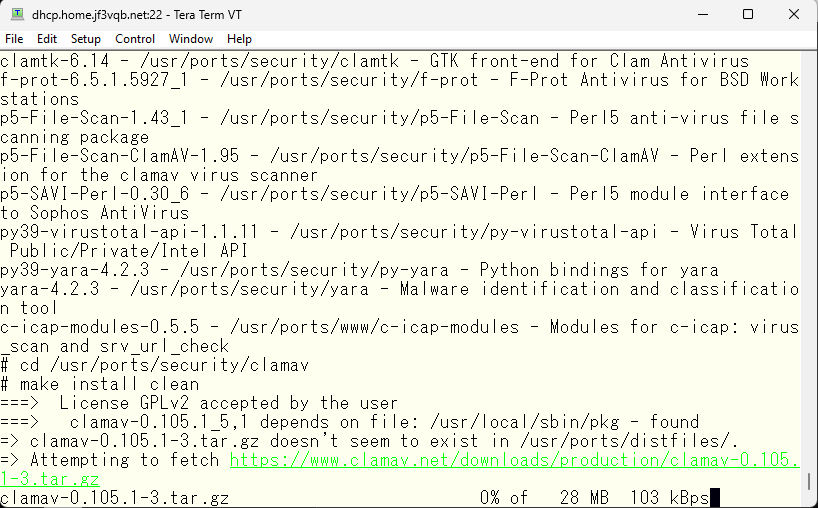
As the server dhcp is a very old 32-bit machine, it took more than an hour to compile.
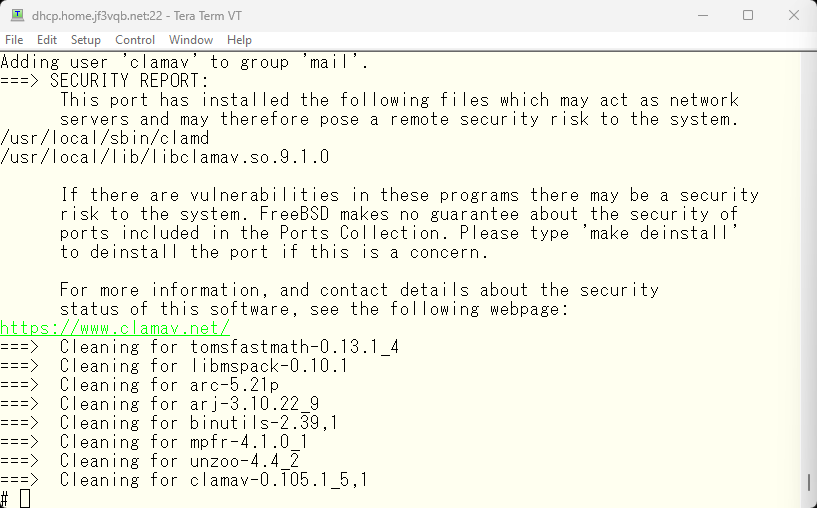
The biggest issue I faced was the memory shortage. It took over 30 minutes to start the engine, and it’s still the same situation, due to insufficient memory.
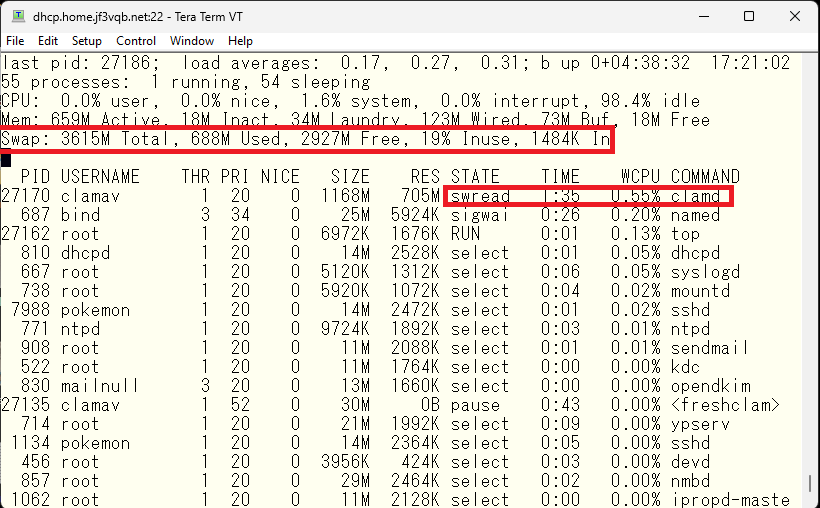
While waiting for the engine to start, I have completed the installation on the server wordpress with enough memory, so I will clean up the installation on the server dhcp.
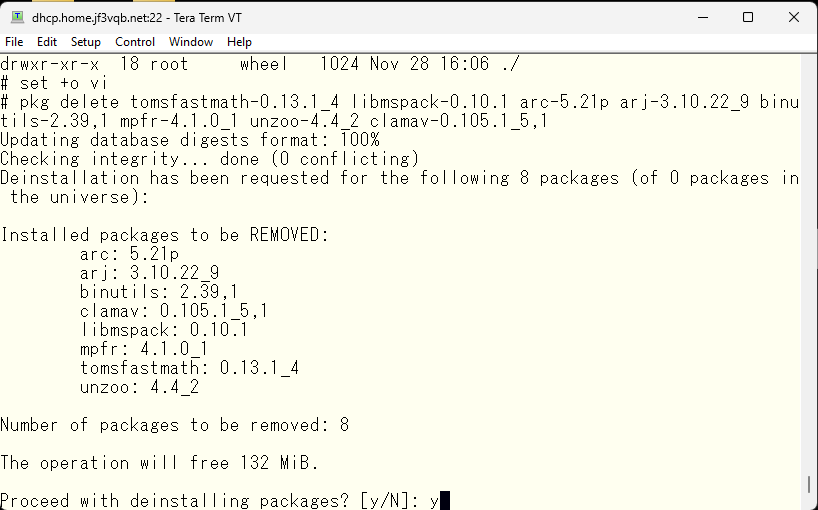
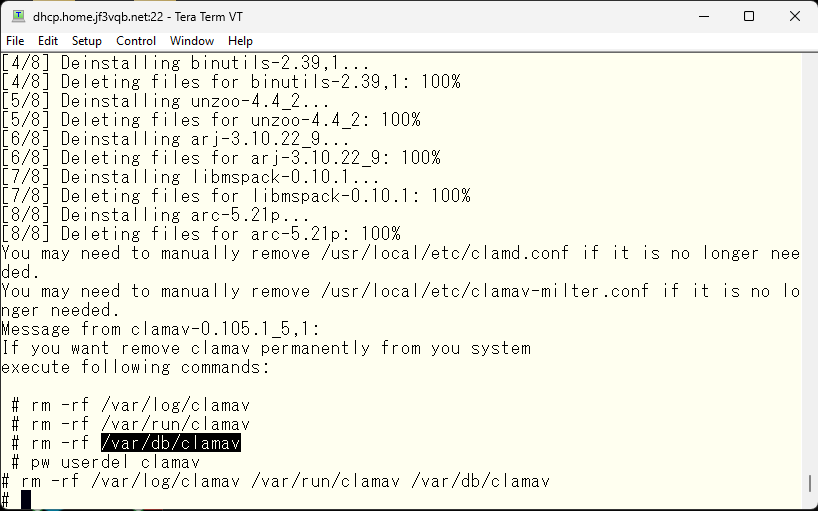
I will also delete the data directory. The user will use it through NIS on wordpress, so I will leave it as it is.
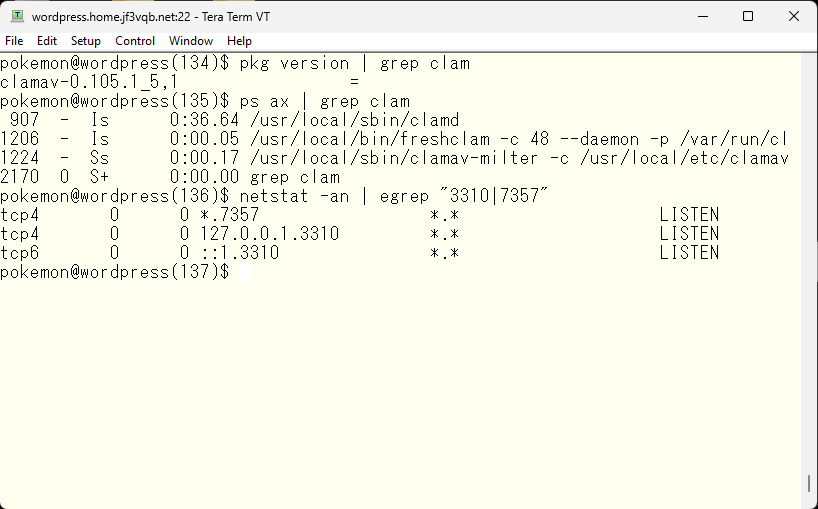
This is the situation on the server wordpress. There are three processes and two open TCP ports. The engine is running on localhost port 3310 and the MILTER is running on TCP port 7357 on an IP address assigned to the NIC, as it will be used by sendmail on dhcp over the network, so UNIX Socket cannot be used.
Here are the changes to the configuration file. I think if you understand the purpose, you can immediately understand what to do from the comments in the configuration file.
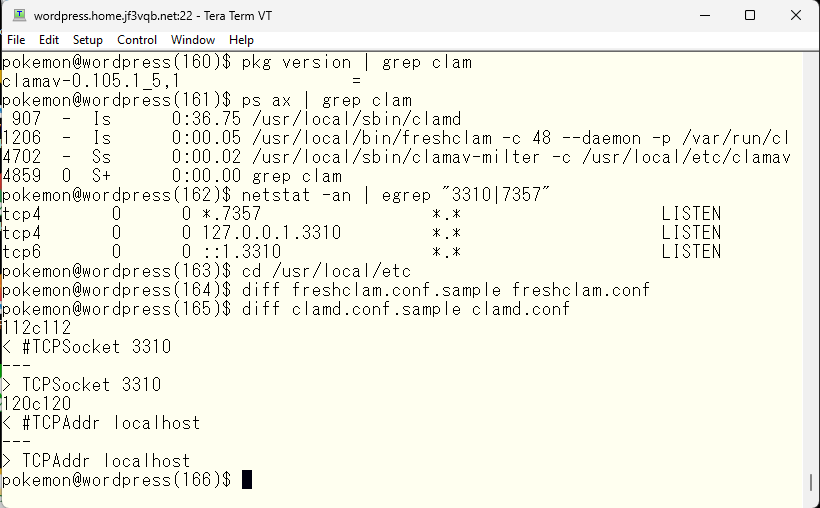
If you use UNIX sockets, in other words if it is only done within the server dhcp, you can use it without making any changes. Unless it is a difficult to run all loads like this experiment or in the case of multiple sendmails for sending and receiving email, it is recommended to run on the same host.
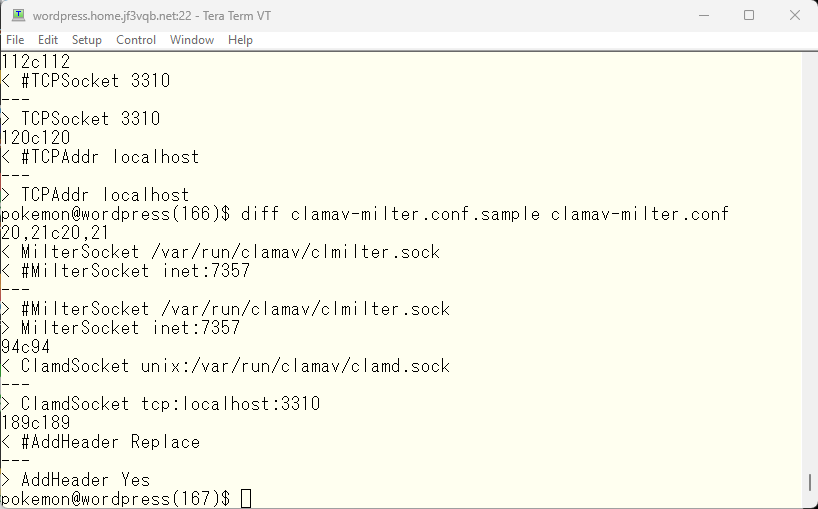
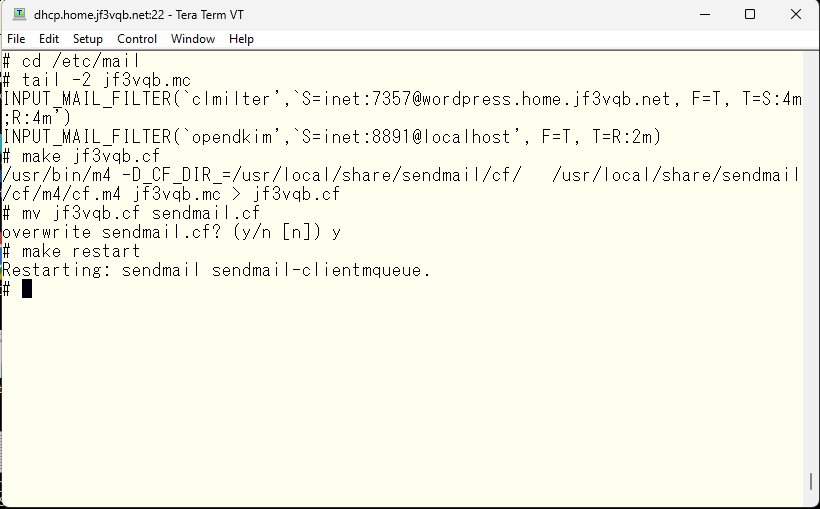
We will configure the MILTER for ClamAV on the server wordpress and rebuild the sendmail.cf to use it.
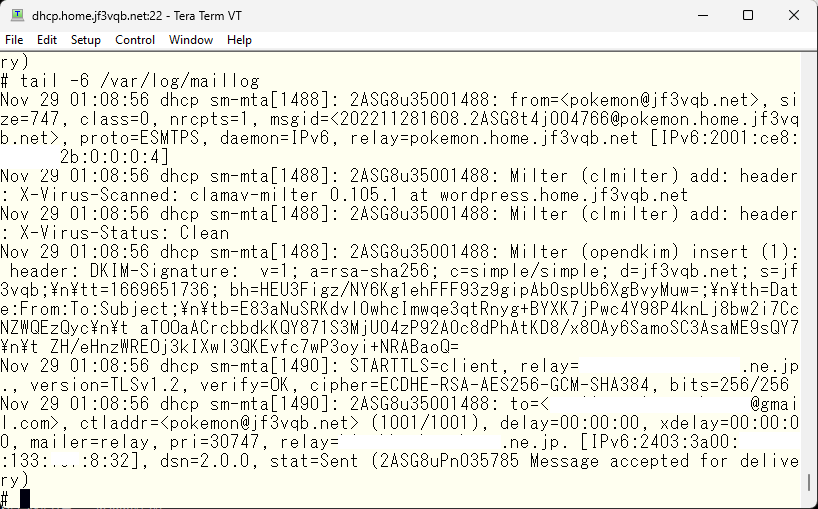
I tried sending an email from pokemon to a test account at gmail.com. The log shows that the email has passed through the clmilter.
This is a cut out of the email header from gmail.com.
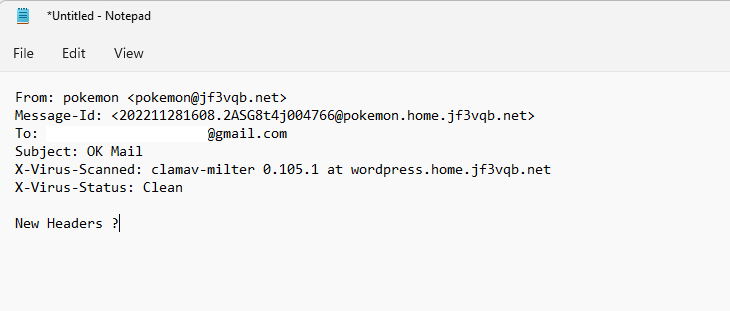
Next, let’s test to see if it will actually block the email by sending a virus. Of course, we can’t use a real virus, so we will test using test patterns. You can download it from here, for example. We only have the OS-included mailx command available so far, so we will download the txt file and paste its content as the email content. It looks like this.
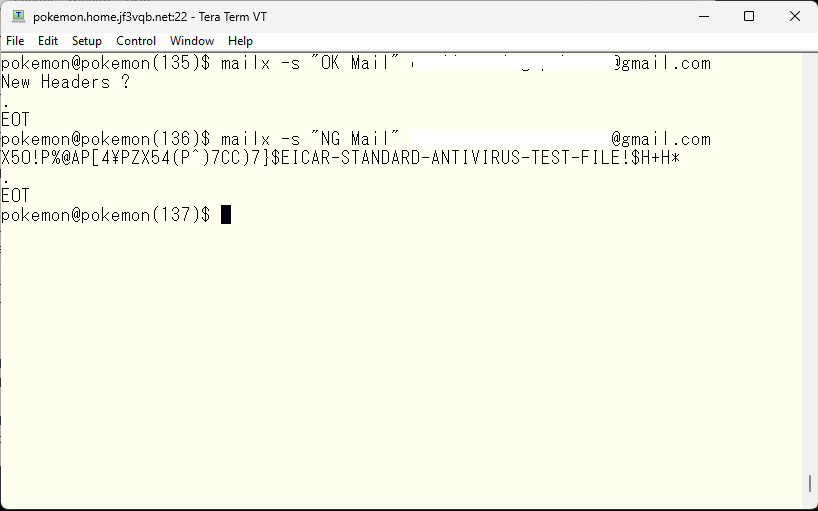
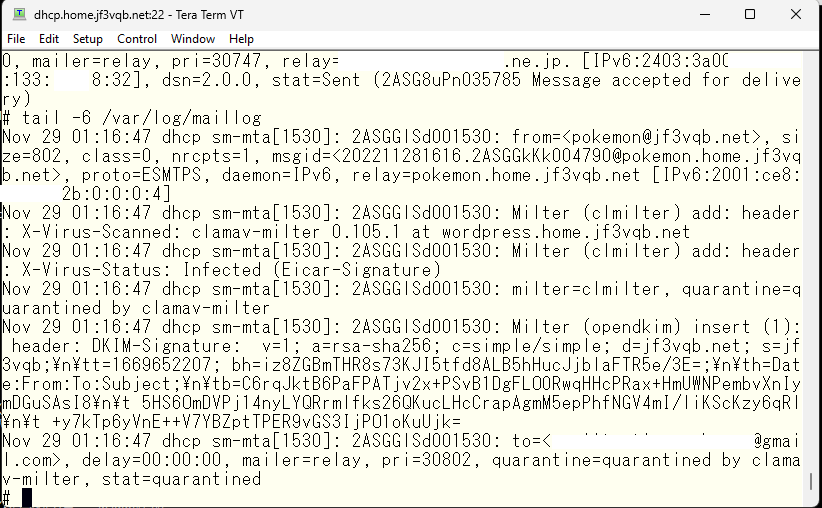
Checking the log shows that the test pattern was infected and the email was quarantined, as indicated by the recorded message.”
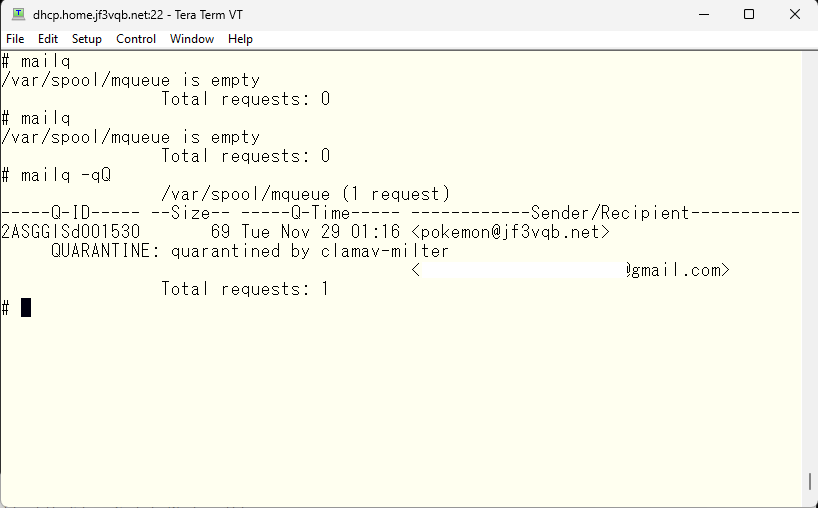
As you can see from running man mailq, you can display the quarantined spool files by using the -qQ option. It would look like this. The quarantined files can be found in the /var/spool/mqueue directory. There are two files for each email. You should delete both of them.
With this, I think the security of email messages can be secured for the time being. I hope to write about DMARC and SPF next time
Advertisement below